Intensification of Information Security | ACER ESG
Corporate information security management strategy and framework
To effectively manage information security, the Corporate Information Security Organization hosts regular meetings every two weeks and examines the applicability of information security policy and protective measures according to the PDCA mechanism. Every year, Acer ensures the implementation is compliant with standards and protects confidentiality, integrity, and availability via internal and external audits. The ISMS focuses on the management of information security risk; mitigates the information security threats in terms of the systems, techniques, and processes; and establishes confidential information protection services that meet our customers’ requirements.

Apart from the ISMS, from 2021, Acer is making reference to the NIST Cybersecurity Framework (CSF) to enhance multi-layer information protection, covering the five major aspects of information security: identification, protection, detection, response, and recovery. Acer thus implements the cyber security life cycle risk management and gradually imports innovative information security techniques, incorporating information security control mechanisms into the maintenance of software and hardware and our daily operational procedures. In doing so, Acer systematically monitors our information security, leveraging NIST CSF to continuously evaluate its maturity.

Monitoring of Information Security Performance
Acer continues to respond to information security risks via third-party assessment and come up with corresponding correction plans. We also commission external specialists to conduct assessments of the maturity of our intranet and information security, ensuring our information security mechanism conforms to industry standards.
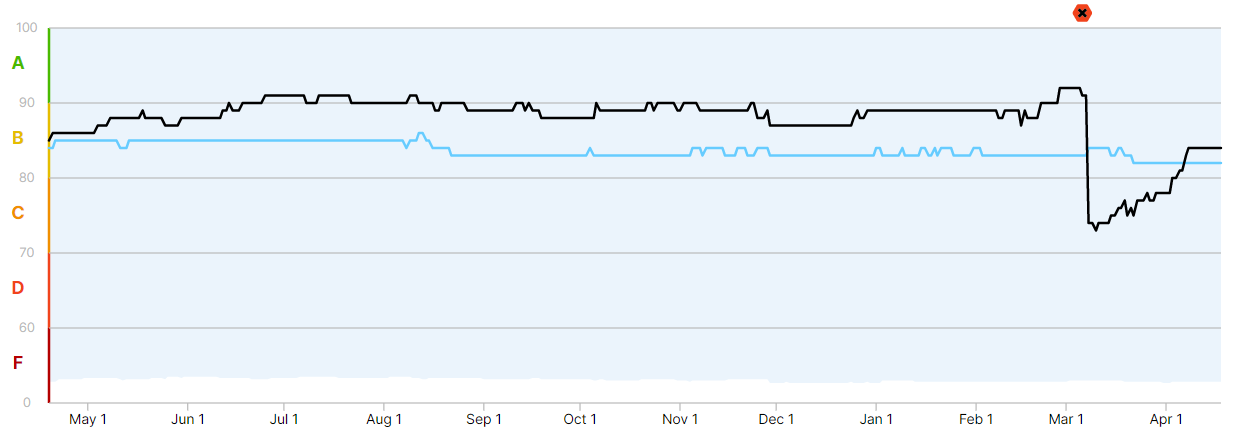
- The blue line on the graph below represents the industry standard, which roughly fits a score of 83, a B level of maturity.
The black line, meanwhile, represents Acer’s performance. It has consistently maintained a performance level above the industry average since May 2022, with a score of 88, surpassing the market average of 83 points.

Investments in the cyber security management
Performance of Information Security Implementation in 2022
01 | Policy
Add/revise 51 ISMS guidelines/policy/procedures/forms
02 | Certification
- Pass ISO/IEC 27001:2013 certification in 2019
- Pass ISO/IEC 27001:2013 recertification in 2022
03 | Communication
6 training video
Create 6 training videos and host 9 meetings/workshops to convey the related rules and importance of ISMS
532 employees
Totally 532 employees received ISMS training during the orientation
17 announcements
Totally 17 information security announcements to convey the related rules and importance of ISMS
04 | Risk Control
6711 employees
6,711 employees completed ISMS online training
2 drills
Execute 2 phishing mail drills. The number of participants exceeds 7000
2 tests
Execute 2 DDoS stress tests
9 penetration tests
Executed 9 penetration tests and checked more than 96 targets globally
1 web vulnerability scan
Perform 1 web vulnerability scan, checking 120website URLs
2 OS vulnerability scan
Perform 2 OS vulnerability scans, checking for more than 7198 vulnerabilities
Cyber Security Risks and Response Measures
Acer has established comprehensive information security protection measures for our network and computers, but this cannot guarantee that the computer systems that support our business operation will be completely free from cyber attacks that could cause the loss of important Acer data. Malicious hackers or cyber attacks motivated by geopolitics may introduce viruses, destructive software, or ransomware to the Company’s network systems, interfering with Acer’s operations.

Acer has faced an attack from ransomware from a member of our staff accidentally clicking on a phishing mail, and we may face similar attacks in the future. To prevent damage from such attacks, Acer implements related corrective actions and continually works to optimize our practices. For instance, we have reduced the chances for phishing emails to make it to inboxes; strengthened firewall controls and Internet access to prevent malware from expanding to other zones; implemented multi-layer management of privileged accounts to prevent them from being hacked; introduced leading solutions for compliance auditing; imported new techniques to detect and handle malware; and routinely executed vulnerability scans & fixes and test staff awareness.
The future focus of our information security
 | No leakage of customers’ data.With multi-layer protection, hackers cannot access customer data even if Acer is under attack from ransomware. |
 | Enhance the comprehensive information security and monitoring mechanismIn doing so, we can make cyber attacks more difficult and thus lower the inclination of hackers to attempt them. Acer deploys endpoint detection and responsive software to ensure the visibility of any abnormal behaviors. |
 | Segregate internal systemsAdopt a zero trust framework in the data centers of both regional offices and headquarters and enhance business continuity drills for information systems, mitigating the impact of attacks and enabling systems to recover within a tolerable time. |










